Cybersecurity Best Practices: Safeguarding Your Organizations Digital Assets
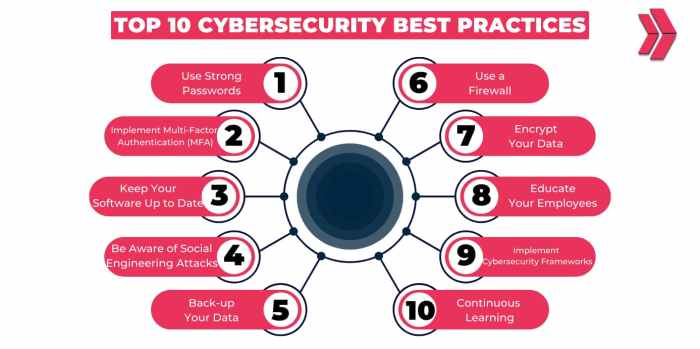
As cybersecurity best practices become increasingly crucial in today's digital landscape, organizations must prioritize implementing robust security measures to protect their valuable data. This guide delves into the essential strategies and principles that can help fortify your defenses against cyber threats.
From the fundamental practices to network security measures and employee training, this comprehensive overview aims to equip you with the knowledge needed to establish a strong cybersecurity posture.
Importance of Cybersecurity Best Practices
Implementing cybersecurity best practices is crucial for organizations to protect their sensitive data, systems, and networks from cyber threats. These practices help in establishing a robust defense mechanism against potential cyber attacks, ensuring the confidentiality, integrity, and availability of critical information.
Risks of Neglecting Cybersecurity Best Practices
- Neglecting cybersecurity best practices can leave organizations vulnerable to data breaches, exposing sensitive information to unauthorized individuals.
- Failure to implement best practices can result in financial losses, reputational damage, and legal consequences for organizations.
- Cybersecurity breaches can lead to operational disruptions, impacting business continuity and productivity.
Examples of Recent Cyber Threats
- The WannaCry ransomware attack in 2017 exploited a vulnerability in outdated systems, affecting organizations worldwide that could have been prevented by timely software updates and patch management.
- Phishing attacks targeting employees through deceptive emails have resulted in unauthorized access to sensitive data, emphasizing the importance of cybersecurity awareness training and email security best practices.
- Data breaches due to weak passwords and lack of multi-factor authentication have compromised user accounts, highlighting the need for robust authentication mechanisms to prevent unauthorized access.
Fundamental Cybersecurity Best Practices

Defense-in-Depth is a cybersecurity strategy that involves implementing multiple layers of security defenses to protect against potential threats. This approach recognizes that a single security measure may not be enough to prevent all types of cyber attacks, so having a combination of security measures significantly reduces the risk of a successful breach.The Principle of Least Privilege is a concept in cybersecurity that limits the access rights of users to the bare minimum permissions they need to perform their job functions.
By restricting unnecessary access, organizations can minimize the potential damage that can be caused by insider threats or compromised accounts.
Regular Software Updates
Regularly updating software is crucial in maintaining cybersecurity as it ensures that known vulnerabilities are patched and security flaws are addressed promptly. Hackers often exploit outdated software to gain unauthorized access to systems, so staying up-to-date with software updates is essential in protecting sensitive data and systems from cyber threats.
Network Security Best Practices
When it comes to protecting sensitive information and ensuring the safety of your network, implementing strong network security best practices is crucial. This involves encrypting data, using firewalls, intrusion detection systems, and secure network configurations.
Encrypting Data in Transit and at Rest
Encrypting data in transit and at rest is essential to prevent unauthorized access to sensitive information. By encrypting data, you are essentially converting it into a code that can only be deciphered with the correct encryption key, making it unreadable to anyone without authorization.
- Use secure protocols such as SSL/TLS when transmitting data over the network to ensure encryption.
- Implement encryption tools and technologies to protect data stored on servers, databases, and other devices.
- Regularly update encryption keys and algorithms to maintain the security of your data.
Firewalls and Intrusion Detection Systems
Firewalls and intrusion detection systems play a critical role in protecting networks from cyber threats by monitoring and controlling incoming and outgoing network traffic.
- Deploy firewalls to filter network traffic based on predetermined security rules and policies.
- Use intrusion detection systems to detect and respond to potential security breaches in real-time.
- Regularly update firewall and intrusion detection system configurations to adapt to evolving threats.
Secure Network Configurations
Organizations can enhance their network security by implementing secure network configurations that limit access to sensitive data and resources.
- Segment your network into different zones with varying levels of access controls to prevent lateral movement by attackers.
- Enforce strong password policies and multi-factor authentication to secure network devices and accounts.
- Regularly audit and monitor network configurations to identify and address potential security vulnerabilities.
Employee Training and Awareness
Employee training and awareness play a crucial role in enhancing cybersecurity within organizations. It is essential for employees at all levels to be well-informed about potential cyber threats and best practices to mitigate these risks.
Role of Phishing Simulations
Phishing simulations are effective tools for raising awareness among employees about the dangers of phishing attacks. By simulating real-life scenarios, employees can learn to identify suspicious emails, links, and requests, thus reducing the likelihood of falling victim to such threats.
Tips for Creating a Cybersecurity Culture
- Provide regular cybersecurity training sessions to educate employees on the latest threats and security measures.
- Encourage employees to report any suspicious activity or potential security breaches promptly.
- Establish clear policies and procedures regarding data security and ensure that all employees adhere to them.
- Conduct periodic security assessments to identify vulnerabilities and areas for improvement.
- Reward employees for practicing good cybersecurity habits and following established protocols.
Incident Response Planning
Incident response planning is a crucial aspect of cybersecurity to effectively handle and mitigate security incidents when they occur. It involves preparing a structured approach to identifying, managing, and responding to security breaches.
Key Components of an Effective Incident Response Plan
- Establishing an incident response team: Designate individuals with specific roles and responsibilities in the event of a security incident.
- Developing communication protocols: Define how information will be shared internally and externally during an incident.
- Creating an incident response playbook: Documenting step-by-step procedures for different types of security incidents.
- Implementing tools and technologies: Utilize software and resources to aid in incident detection, analysis, and response.
Importance of Regular Testing and Updating of Incident Response Plans
Regular testing and updating of incident response plans are essential to ensure their effectiveness when a real incident occurs. By conducting drills and exercises, organizations can identify gaps, evaluate response times, and refine processes to improve overall readiness.
Examples of Successful Incident Response Strategies in Cybersecurity Incidents
- Containment and eradication: Quickly isolating affected systems and removing malicious components to prevent further damage.
- Forensic analysis: Conducting thorough investigations to determine the root cause of the incident and gather evidence for legal proceedings.
- Communication with stakeholders: Keeping internal teams, customers, and regulatory bodies informed throughout the incident response process.
- Continuous improvement: Learning from past incidents to enhance incident response plans and procedures for future incidents.
Final Thoughts
By adhering to cybersecurity best practices Artikeld in this guide, organizations can mitigate risks, enhance their security posture, and safeguard their sensitive information from evolving cyber threats. Stay vigilant, stay informed, and stay secure in the ever-changing digital landscape.
Essential Questionnaire
What is the significance of regular software updates in cybersecurity?
Regular software updates are crucial as they often contain patches for known vulnerabilities that hackers can exploit. By keeping software up to date, organizations can strengthen their defenses against potential cyber attacks.
How can organizations create a cybersecurity culture among employees?
Organizations can foster a cybersecurity culture by providing regular training sessions, promoting awareness through simulated phishing exercises, and encouraging employees to report any suspicious activities. By involving employees in the security process, organizations can create a collective defense mechanism against cyber threats.
Why is encrypting data both in transit and at rest important for network security?
Encrypting data ensures that even if unauthorized parties intercept it, they cannot decipher its contents. This helps protect sensitive information from being compromised and maintains the confidentiality and integrity of data both during transmission and while stored.

